Jul 15, 2025
Your Salesforce org is no longer just a CRM system of record. It's the command center for your entire business, connected to dozens of other systems. And every single one of those connections is a potential security hole. Almost a third of all third-party apps in Salesforce environments have poor security scores. That's right, there's a rock-paper-scissors chance that any given app in your environment represents a significant security risk.
It’s an inescapable reality. Your ERP syncs with opportunity data. Customer service platforms pull account information. AI agents are starting to orchestrate these connections in ways we're only beginning to understand. Connecting these systems isn't a "nice to have", it's fundamental to how a company operates.
Integrations and connected apps are therefore one of the most critical topics for anyone managing a Salesforce instance today, as this is where platform administration, governance, and architecture collide. And with AI agents poised to take on more and more tasks within Salesforce, this nexus is about to get a lot more crowded and a lot more complex.
Here's the uncomfortable truth, every single connection increases your risk surface. For any integration to be called a success, it must check four boxes: scalability, security, data consistency, and maintainability. None of these are negotiable.
Your First Line of Defense: The Admin and the Architect
Before diving into the weeds, it's crucial to establish that security is a shared responsibility. It can't be passed off to a single team. That being said, in the world of Salesforce, two key roles form the core of defense:
The Salesforce Admin - The Gatekeeper: The admin is on the front lines, holding the keys to the kingdom. Responsible for the day-to-day tactical work - installing apps, managing user access, and implementing security controls - they serve as the first line of defense.
The Salesforce Architect - The Strategist: The architect is the grand planner who sees the whole chessboard. They design the security framework, define integration protocols, and create the governance processes for the admins to execute. They think in terms of long-term risk, scalability, and the overall health of the platform.
These two roles, working in concert, are the guardians of the org. But they face a constant, relentless challenge.
The Unwinnable Tug-of-War: Move Fast or Stay Secure
Here is a familiar scenario: The sales team just signed a contract for a new tool that promises to triple their pipeline. They need it integrated yesterday. To the sales team, security reviews, sandbox testing, and cautious questions are often seen as nothing more than bureaucratic red tape.
The admin or architect is caught in the middle. They understand the risks and know what happens when a poorly vetted app gets access to sensitive data. But the pressure from the business is immense, creating a fundamental conflict: balancing the business's need for speed with the responsibility to ensure safety. This tension often forces technical leaders into the uncomfortable position of being the "bad guys," the people who have to say "no" or, more frustratingly, "not yet."
This pressure leads teams to take shortcuts, and those shortcuts expose some major pain points in the traditional way we manage third-party applications.
The Headaches of "Integrations as Usual"
Managing connected apps and managed packages the old-fashioned way is, frankly, a potential nightmare. It’s a collection of manual processes, educated guesses, and crossed fingers. These challenges are likely familiar to anyone managing a complex Salesforce instance.
Permission Complexity: Salesforce's permission model is powerful, but it gets exponentially more complex with every managed package installed. Trying to understand how package permissions, profiles, permission sets, and sharing rules interact is like untangling a drawer full of old headphones. It requires a level of expertise that many teams don't have the time to develop.
Time-Consuming Vendor Assessments: Doing the right thing and properly vetting a new vendor can mean days, or even weeks, spent chasing down security documentation, trying to decipher a SOC 2 report, and translating it all into something that makes sense for the org. It’s a massive time sink that delays projects and frays nerves.
The Dreaded Update Cycle: Security management doesn't stop at the initial install, it's a full lifecycle. Teams have to track security updates for a dozen different packages, figure out if an update will break an existing setup, and then coordinate testing and deployment across sandboxes and production. It’s a significant, ongoing administrative burden.
Unchecked Integration Sprawl: As a company grows, so does its number of apps and integrations. Without strong governance, an org can become a tangled web of connections, many of which might be redundant, unused, or insecure. And, remember, the attack surface grows with every new connection.
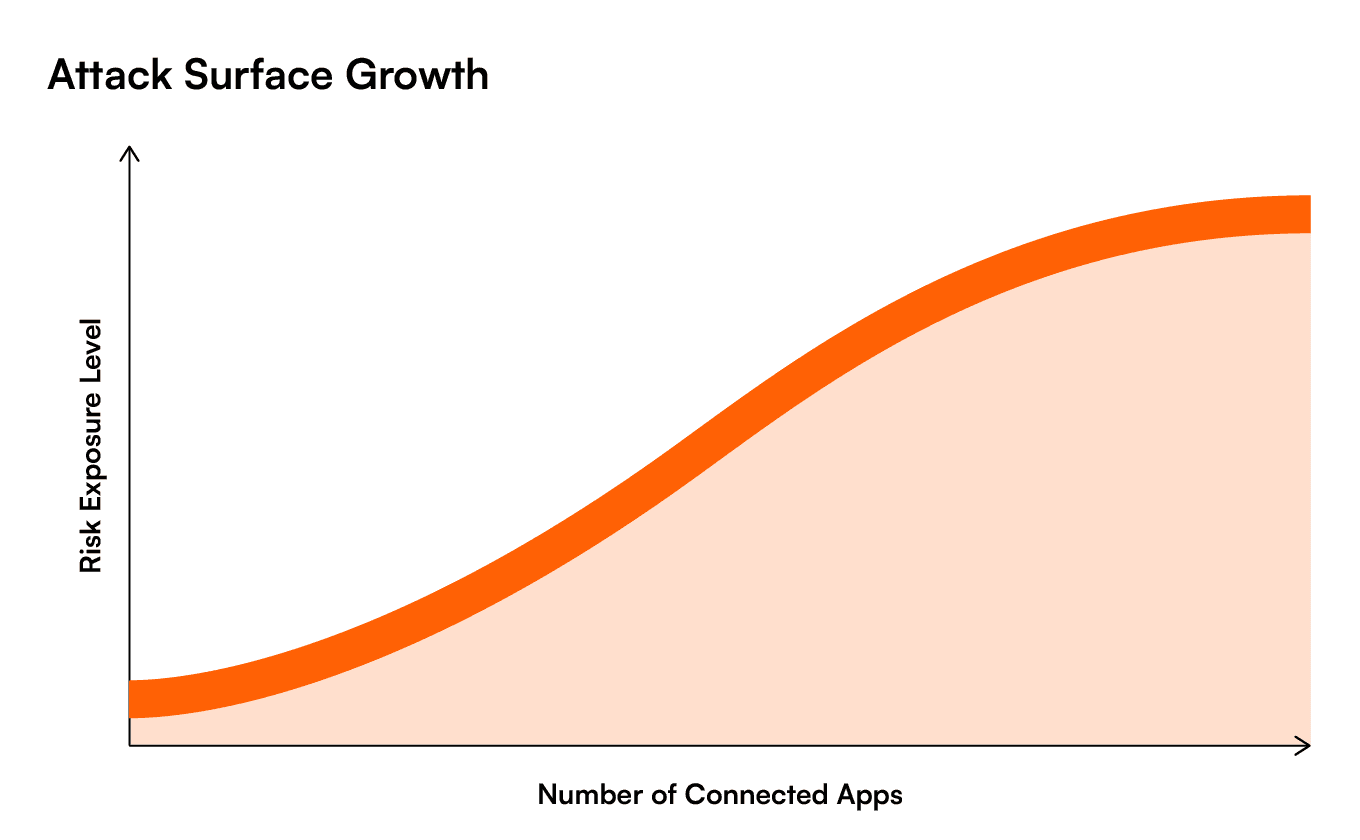
The Compliance Maze: How does that new e-signature app affect GDPR or HIPAA compliance? Is its data handling aligned with the company’s data retention policies? Mapping third-party app functionality to complex regulatory requirements is a persistent and high-stakes challenge.
Visibility and Control Gaps: Apps often ask for broad permissions during installation. To be fair, Salesforce OAuth scopes are broad and don’t allow for granular access control at the object level, typically granting wide API access.Salesforce’s recommendation is that after an app is granted API access, the integration user should be assigned a permission set that grants access only to the specific objects the app needs. This process can be labor-intensive, leading many admins to forgo it (see Permission Complexity above). This leaves open the question “what is that app actually doing?” Is it just accessing the Lead records it needs, or is it quietly scanning every field on Opportunity and Account objects? When left unchecked, this is a big blind spot.
There has to be a better way. And there is.
Enter Security Scoring: Your Integration Report Card
What if all that complexity—the vendor assessments, the permission analysis, the compliance mapping—could be boiled down into a single, easy-to-understand metric?
That’s the power of a scoring approach.
By assigning a security score to every application and integration connected to an environment, the entire process is simplified. A score can algorithmically combine dozens of security best practices into a single number or grade. It provides a common language that admins, architects, and even business stakeholders can use to make informed, risk-based decisions quickly.
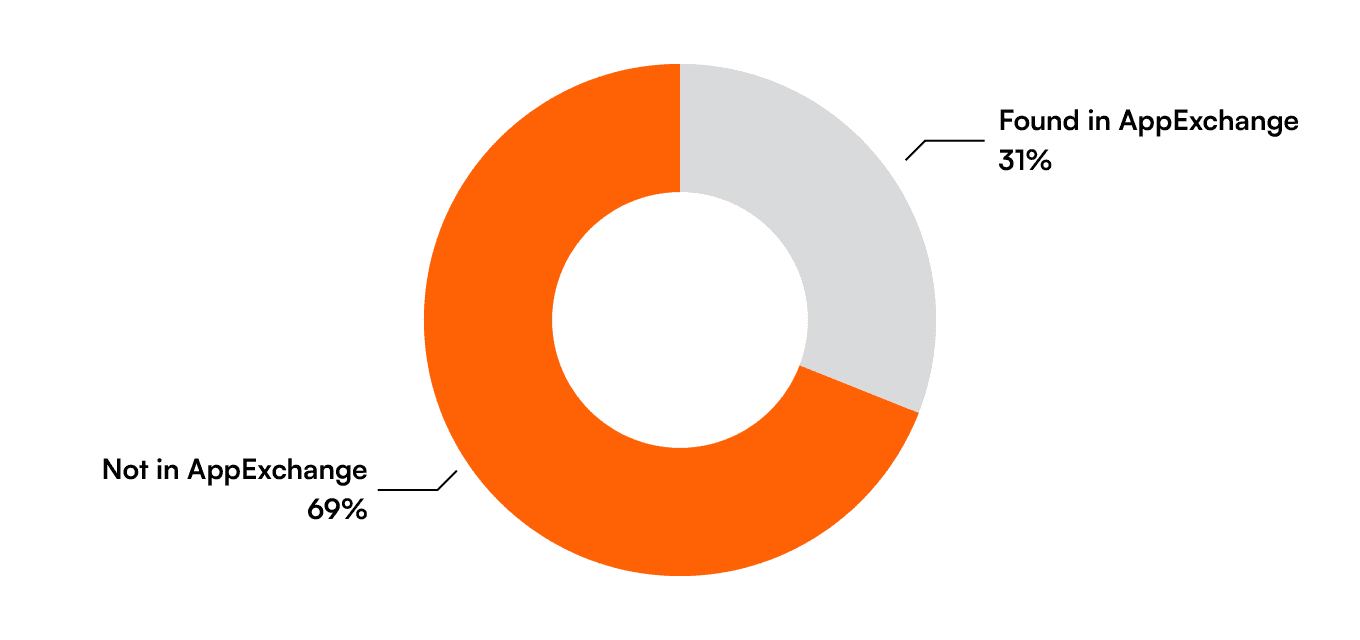
This is a concept we've put into practice here at Valo. Using Valo AI, we’ve scored many thousands of integrations in customer environments, and the results have been eye-opening: Over one-third of all the third-party apps we analyzed have a poor security score.
That’s a sobering statistic. It means that in a typical Salesforce org, there's a significant chance that any given app represents a significant security risk. So, what’s behind these poor scores?
Peeking Inside the Black Box
To understand why so many apps score poorly, it's important to first understand what we're dealing with. From a security perspective, there are two main categories of applications in the Salesforce ecosystem.
Managed Apps: These are the packages installed directly from the AppExchange or another source into an org. The vendor bundles all the components—objects, Apex code, Lightning pages—into a container. While convenient, this container is often a "black box” and it's nearly impossible to be 100% sure what it's doing. Managed Packages generally receive better security scores as they are created by companies, they have gone through security review by Salesforce, and Salesforce requires some basics like a security policy. That being said, at Valo, we have identified problematic managed packages.
External Apps: These are outside systems (like an ERP or a marketing platform) that connect to Salesforce through the API. This access is controlled using a Connected App, which acts as a gatekeeper, defining how that external system can authenticate and interact with data. But this, too, is a kind of black box. The API calls coming in and out are visible, but there is no visibility into the business logic or security practices of the system on the other end.
Admin Tools: Often taking the form of browser extensions or similar, these apps are mostly created by Salesforce enthusiasts and often used by people with a Salesforce Administrator profile. Many Valo customers have told us that they couldn’t live without some of their admin tools and we appreciate the value they can bring to the job to be done. That being said, given that browser extensions are a wild west of security it’s best to carefully grade these tools.
Sales Tools: Another group are different mobile apps and other sales tools that Salesforce users connect to Salesforce. These are never Managed Packages as normal users cannot install managed packages. At Valo, we often see in our customer environments that there are old tokens from many years ago active for such tools. In the past, security was even less strict than it is today and Connected App tokens never expire by default in Salesforce.
“But Isn’t Everything on the AppExchange Secure?”
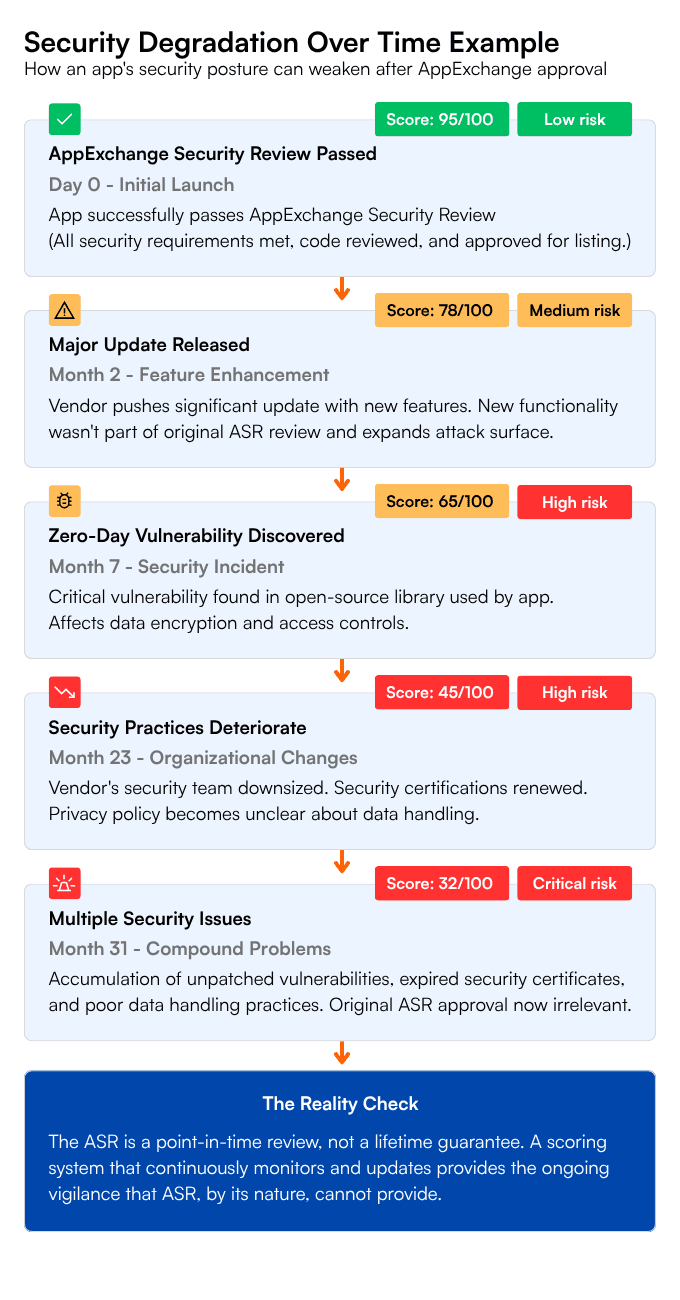
This is a frequent and understandable question. Anyone new to the Salesforce ecosystem might rightly point out that these apps had to pass the AppExchange Security Review (ASR) to get listed.
They did. And the ASR is a critical and valuable part of the Salesforce ecosystem. But it is not, and was never intended to be, a lifetime guarantee of security.
The single biggest issue is that the ASR is a point-in-time review. An app gets reviewed and approved, and then it gets listed. But what happens next?
The vendor pushes an update a month later with new features and new code.
A new, zero-day vulnerability is discovered in a common open-source library that the app uses.
The vendor’s own internal security practices weaken over time.
The ASR isn't a continuous, real-time audit. This leads to a false sense of security, where teams assume an app is secure forever simply because it passed the ASR once and is why the "install and forget" mindset is so risky. A scoring system that is continuously updated provides the ongoing vigilance that the ASR, by its nature, cannot.
How to Evaluate an App’s Security Posture
A robust security score isn't just a random number. It's a weighted assessment based on a holistic view of the application vendor's security posture. It looks beyond the code to evaluate the company and its practices. Here are some of the key ingredients that should go into any good security score:
Proper Data Handling: Does the app have unclear or problematic privacy policies and data retention practices?
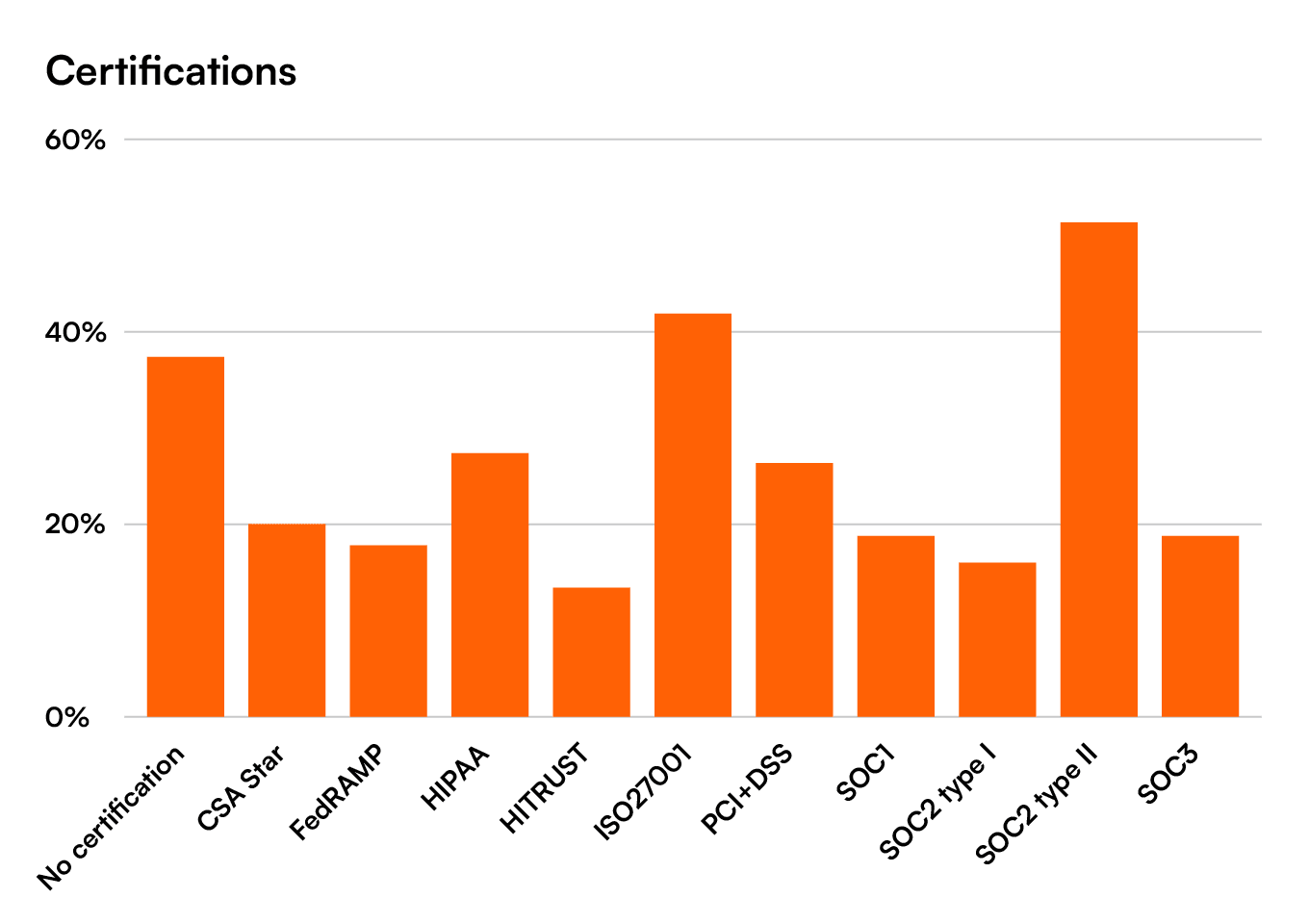
Security Certifications: Does the vendor maintain industry-standard certifications like SOC 2 Type II, ISO 27001, or others relevant to the industry? This is third-party validation of their controls.
Privacy Policies: Is their privacy policy clear, comprehensive, and compliant with regulations like GDPR and CCPA? Does it clearly state what data they collect and how they use it?
Terms of Use: Are the terms of use fair? Do they try to limit their liability to an unreasonable degree?
User Reviews: What are other customers saying? Close attention should be paid to reviews that mention security issues, bugs, or poor support.
Vetting Processes: Has the app been vetted by more than just the ASR? Are they listed in other curated marketplaces with their own security standards?
Bug Bounty Programs: Does the company run a public bug bounty program? This shows confidence in their security and a commitment to working with independent security researchers to find and fix flaws.
Goldilocks Access: Does the app request the 'just right' amount of permissions (the principle of least privilege)? Over-permissioned apps that ask for access to everything are a major red flag. A secure app follows the principle of least privilege, requesting access only to the data it absolutely needs to function. It’s worth noting that this is one of the more challenging criteria to score an app on. The reason is that scans alone cannot see the access scope the app requested (for most apps). Salesforce doesn't allow us to see it so simply. So, the only way to evaluate it is to install the app directly and take a screenshot of the "This app is asking to" OAuth scope dialog.
Sufficient Monitoring: Does the app lack proper logging and audit capabilities? Scoring this criterion, requires actually using the app and seeing what options are.
The High Cost of a Low Score
Allowing a low-scoring application into a Salesforce environment doesn’t just introduce a piece of software; it introduces risk. The potential consequences are severe.
Data and Credential Exposure: A poorly secured third-party app can become a gateway to an org. The vendor might be downloading sensitive data to their own servers or storing API credentials with weak protections. Trust is extended, and a breach on their end becomes a breach on your end.
Vulnerability to Breaches: Hackers are increasingly targeting the software supply chain. Instead of attacking a well-defended company directly, they attack a smaller, less secure vendor that provides software to that company. There are countless examples of major breaches that started with a compromised third-party tool.
Trojan Horse Risks: While rare, an application could be designed as a trojan horse from the start. More commonly, a malicious actor buys a low cost Chrome extension or a mobile app (maybe for a few thousand dollars, maybe even for free) from a developer who is no longer willing to keep updating it and is looking for someone to continue the work. The malicious actor then pushes a compromised update.
Regulatory Nightmares: For organizations in regulated industries, using insecure third-party software can create direct violations of frameworks like HIPAA, NIST, DORA, or PCI DSS. A security incident could lead not only to a loss of customer trust but also to crippling fines.
Trade Suspicion for Strategy with Valo AI
Failing to properly assess the security of the applications connected to or installed in Salesforce is one of the single greatest risks facing an organization today. In our hyper-connected world, extending trust and data access to unknown entities is not a viable strategy.
A thorough vetting process is not optional; it is essential.
But it doesn't have to be a bottleneck. By adopting a scoring approach, the process is transformed from a slow, manual, and often subjective task into a fast, data-driven, and strategic function. It gives admins and architects a simple, powerful tool to quickly assess risk, enabling them to say "yes" to the business more often and with more confidence.
This is precisely where Valo AI comes in. While the scoring methodology is incredibly powerful, manually doing all that scoring (and doing it continually!) is a monumental task. Valo AI does the hard work automatically. It continuously discovers and analyzes every integration, managed package, and connected app in the Salesforce environment. It digs in to generate a dynamic up-to-date security score for every integrations.
Valo AI transforms your security work. Instead of spending weeks on manual vetting, you get a continuously updated security score for every app in your environment.
This frees your team from being the 'Department of No' and empowers them to be strategic partners who drive the business forward, safely.
Ready to see the security scores of your integrations? It’s easy with Valo AI. Simply connect your environment to Valo’s free trial and Valo will immediately start scoring.



