Aug 27, 2025
Salesforce administrators, platform architects, and security teams face an escalating threat landscape that demands immediate attention. August 2025 has marked a significant shift in cybercriminal tactics, with the emergence of a sophisticated partnership between two prominent threat actors: Scattered Spider and ShinyHunters.
Critical Security Alert
This isn't just another security update; it's a critical alert. In the past few weeks, we've seen a significant, coordinated shift in cybercriminal tactics targeting Salesforce customers. Many large enterprises, brands you know and trust like Cartier, Adidas, Coca-Cola, and even Google, have disclosed hacks of their Salesforce environments. Check out this partial list:
Qantas
Air France
KLM
Coca-Cola
Allianz
Aflac
Marks & Spencer
Google
Cisco
Cartier
LVMH
Harrods
Pandora
Adidas
Hawaiian Airlines
Workday
Chanel
Dior
Tiffany & Co.
This is an update to our previous post on Scattered Spider, made necessary by the alarming new collaboration between these social engineering specialists and the notorious data extortionists, ShinyHunters. This partnership represents a more dangerous, coordinated threat than what we reported before.
Let's untangle this web together and understand the threat, how it works, and what you can do to protect your organization.
The Threat: 'Access-as-a-Service' Meets 'Extortion-as-a-Service'
At the heart of this campaign is the collaboration between two now infamous groups: Scattered Spider and ShinyHunters. This alliance has created a viciously effective cybercriminal partnership.
Scattered Spider: The Frontline Attackers
Think of Scattered Spider as the reconnaissance and infiltration specialists. This decentralized network of cybercriminals, often native English speakers from the US and UK, are masters of social engineering. Emerging around 2022, this group, also known as UNC3944, quickly made a name for itself with tactics like vishing (voice phishing), SIM swapping, and MFA fatigue attacks.
They are incredibly convincing on phishing calls, now specializing in "vishing" to gain that initial foothold into Salesforce environments. Their track record is notable, with high-profile victims including MoneyGram, Transport for London, Caesars, MGM Resorts, Clorox, DoorDash, Twilio, Reddit, Coinbase, MailChimp, Okta, HubSpot, Cloudflare andActivision. In this new partnership, they provide the "Access-as-a-Service," getting their partners through the door.
ShinyHunters: The Monetization Engine
Once Scattered Spider has the data, ShinyHunters takes over. This group is the monetization and extortion arm of the operation. Known for large-scale data breaches, their role is to transform stolen data into cash, effectively running an "Extortion-as-a-Service" model.
ShinyHunters, also tracked as UNC6040, burst onto the scene in 2020 with a series of major data breaches and extortion campaigns, hitting global brands like AT&T, Microsoft, and Ticketmaster. They are known for their assertive self-promotion.
Even with law enforcement making arrests in late 2024 and mid-2025, the attacks have continued without pause. This persistence shows a fundamental evolution; ShinyHunters operates not as a single gang but as a decentralized collective. This structure allows affiliates, like Scattered Spider, to carry out attacks under the ShinyHunters name. They've even used a combined alias, "Scattered Spider LAPSU$ Sp1d3r Hunters," on Telegram for a while, a supposed crossover with yet another cyber criminal group LAPSUS$.
How It’s Happening
So, how exactly are they pulling this off?
The attackers are exploiting the human layer. They are exploiting the trust and security gaps between users, their identities, and application configurations.
The attack usually unfolds like:
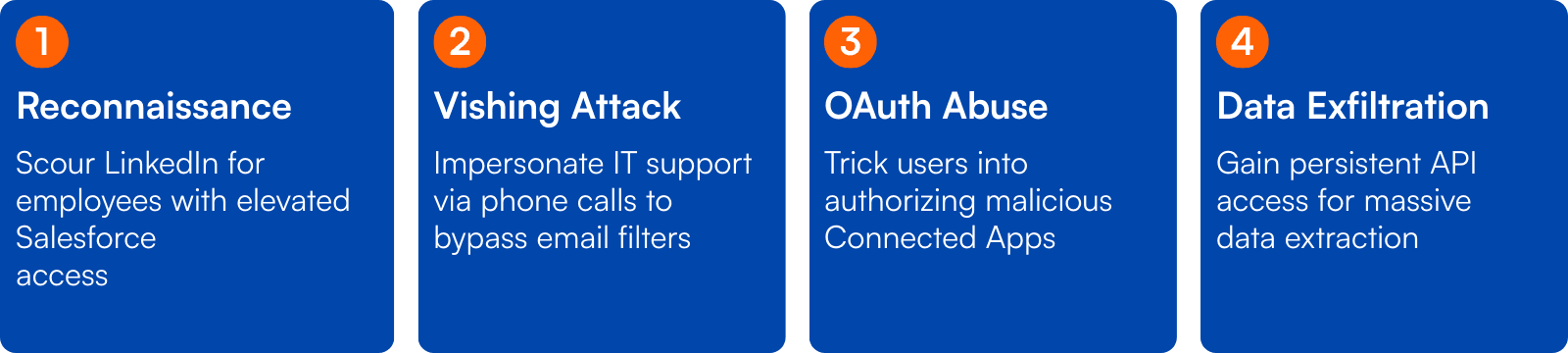
Step 1: Reconnaissance & Impersonation
The campaign starts with reconnaissance. Attackers scour public platforms like LinkedIn to find employees. All public indicators are that the attackers are going after employees with limited and specific data access. There are no indications that the attackers gained admin access in any of these cases. Instead, the attackers call support, and a third-party, Tier 1 agent picks up the phone. These agents almost always have a Salesforce account with visibility to customer data like invoices or financial balances.
Step 2: The Vishing Attack
The main attack vector is a "meticulously planned voice phishing" (vishing) call. The attacker, often impersonating IT support staff (a role that inherently commands trust) calls the targeted employee. This approach cleverly bypasses traditional email security filters and creates a live, interactive environment ready for social engineering. The attacker then directs the employee to a fake login portal or a Salesforce Connected App setup page.
Step 3: OAuth 2.0 Abuse and Connected App Exploitation
During the call, the attacker walks the employee through what seems like a routine process: entering an eight-digit connection code. This action, however, initiates an OAuth 2.0 authorization flow for a malicious "uninstalled" Connected App that the attacker controls. This malicious app is often disguised as a legitimate tool, like a data loader. However, in some cases the likely app they use IS actually the Salesforce Data Loader - a dual use tool in a way. Data Loader is a desktop executable. You can run it on any computer. It's also open source. Source code is in Github.
The moment the user approves the app, the attackers gain persistent API access tokens with that user's permissions, effectively giving them a backdoor into the environment.
Step 4: Data Exfiltration & Monetization
With persistent API access, the attackers can now query and export massive amounts of data from the Salesforce environment. They often start small, with low-volume queries to avoid suspicion, before ramping up to bulk data extraction. They employ a "delayed extortion" model, in some cases waiting weeks or months before activating.
Salesforce Responds
Salesforce had to respond, and they did. Around 6 a.m. Pacific Time on Tuesday, August 19th, they emailed much of their customer base about upcoming changes. They also added a warning to the primary authentication page being exploited.
Here’s a breakdown of the changes Salesforce is making:
Starting early Sept, Salesforce will be progressively rolling out a change in its policy on connected Apps. This will be a rolling release with different customers seeing the change at different times.
With this change, users will need the "Approve Uninstalled Connected Apps" permission to use uninstalled apps. If API Access Control isn't enabled, the "Use Any API Client" permission will be required. If it is enabled, only "Use Any API Client" will grant this access.
Salesforce is also making a strong recommendation that all review their connected apps. This is something that’s a lot of work to do manually but can be accomplished easily with Valo (more on that below).
The goal of these changes is to ensure that only apps with strong security scores, known functionality, and active users are permitted.
Your Defensive Playbook: Augmenting Security with Activity Observing Via AI
So, what can you do right now? Start with these critical, foundational security measures.
Culture: This is where it always begins. Promote a security-first culture. Train users, especially customer support teams with broad data access, to spot vishing and social engineering attempts.
Permissions: Apply the principle of least privilege. Don't grant permissions users don't absolutely need.
Monitoring: Leverage tools like Salesforce Shield's Real-Time Event Monitoring and Login Forensics to gain insights into suspicious login patterns and unusual data exports.
The Beauty and Agony of Manual Audits.
Conducting manual audits of your Salesforce environment with tools like Salesforce Shield is an absolutely essential part of a strong security strategy. It's the foundational work that demonstrates a serious commitment to protecting your organization's data. This diligence is the necessary first step, providing a critical snapshot of your security posture at a specific moment in time.
Revving all connected apps with solutions like Salesforce Shield is a way to prepare for the upcoming Salesforce changes. However this is a manual approach and there is a challenge with manual audits - the sheer amount of work they take. In today's complex Salesforce environments, manually cataloging and vetting every single connected app is a monumental task that most organizations simply don't have the resources for. Valo AI vastly reduces the work by fully automating connected app checks.
The Valo Solution: Automated AI Intelligence for Modern Threats
Valo AI is designed to combat these exact challenges.
Automated Security Scoring: Valo AI continuously discovers and analyzes every connected app in your environment, providing an instant, data-driven security score. Valo AI is always watching.
Beyond Posture, Into Activity: Valo AI doesn't just look at configurations; it monitors what each app is actually doing. It alerts of any anomalous behavior.
AI-Powered Permission Tightening: Valo's AI also analyzes user activity to intelligently suggest where you can safely tighten permissions without breaking critical workflows. This directly combats the "user access request fatigue" that leads to over-provisioning.
Take Control of Your Salesforce Security
The attackers have evolved. A reactive, manual approach is no longer enough to protect your organization. You cannot afford to wait for the next attack headline. The time to act is now. Start by auditing your apps and tightening your permissions.
Ready to see how your environment scores? Valo offers a 30-day free trial on the AppExchange. In minutes, you can discover which of your connected apps might be hiding dormant threats.